Implementation of Blockchain in Java
RVCE
This project focuses on building a secure and efficient blockchain system using Java, with the aim of validating, processing, and ensuring the stability of data blocks. A Java class was programmed to handle data validation, calculate hash values for the current blocks, and ensure the integrity of the blockchain. To further enhance the system's robustness, an algorithm was designed to detect and address potential corruption by dynamically modifying block values. This method tests the stability of the blockchain, simulating real-world scenarios where data corruption might occur, thus ensuring the system's resilience and security.
Overview of Blockchain Technology
Introduction to Blockchain
Blockchain is the core technology behind Bitcoin and other cryptocurrencies. It is a distributed database of records or transactions shared among multiple parties. Each transaction is verified by the majority of participants.Blockchain is a distributed ledger that records transactions across a network of computers. These transactions are secured using cryptographic methods and are verified by the majority of the network participants.
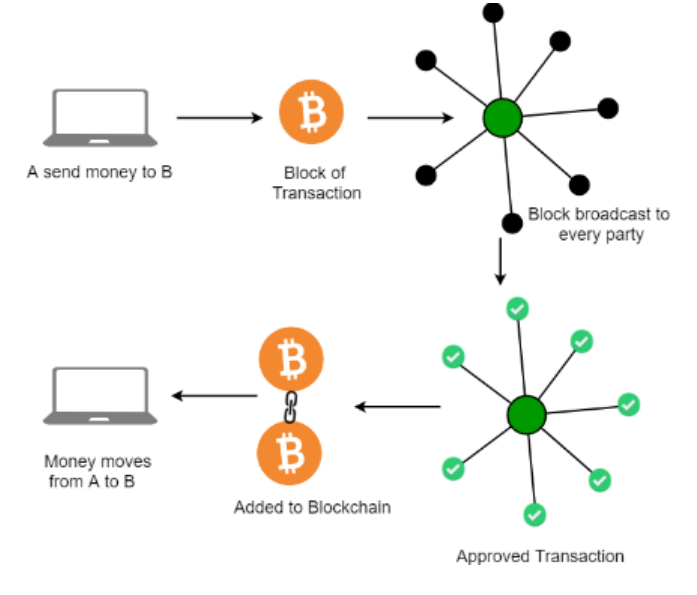
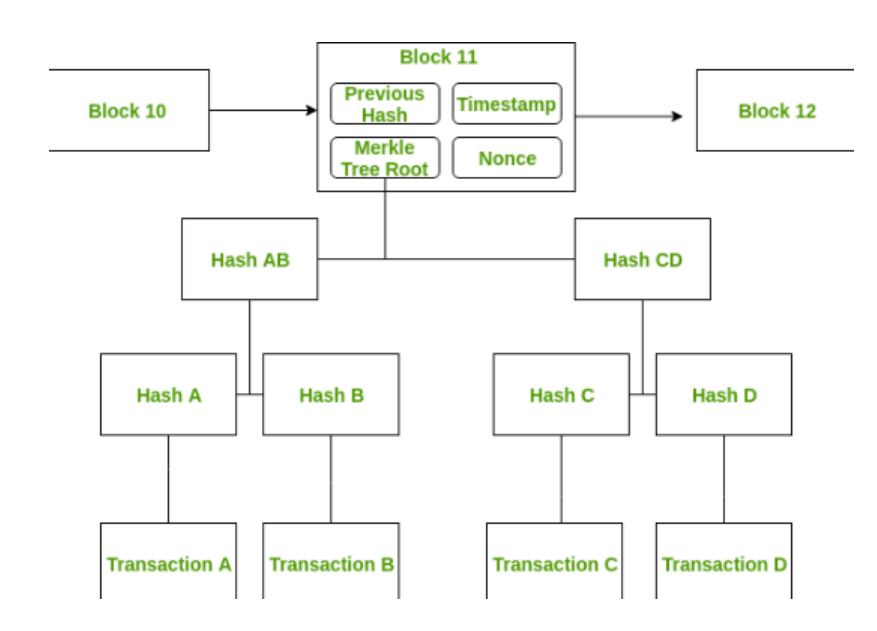
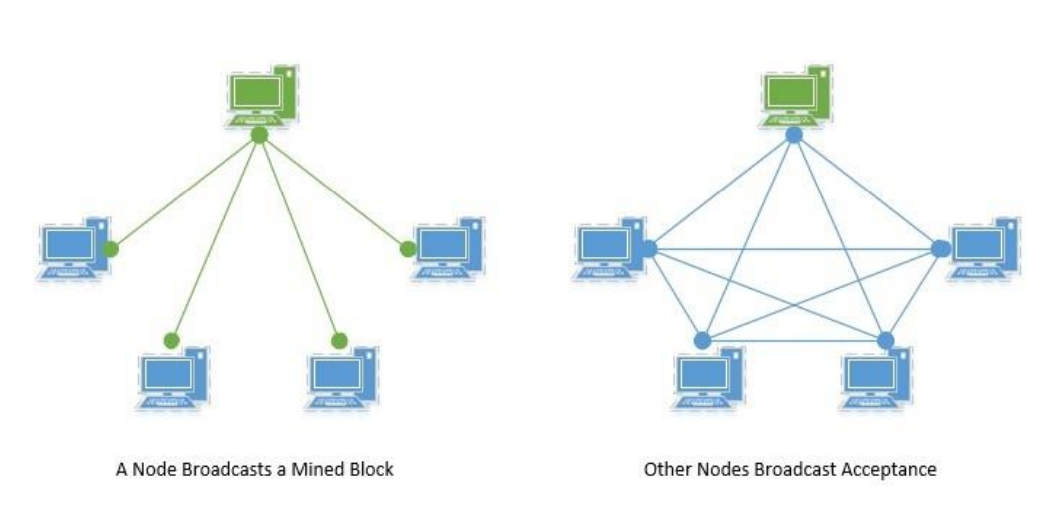
Each block in a blockchain is comprised of several key components: the Previous Hash, which links to the hash of the preceding block; a Timestamp that records the moment the block was created; a Nonce, calculated by miners through cryptographic puzzles as part of the proof of work; and the Merkle Tree Root, which efficiently and securely verifies the integrity of the block's data. The process of mining involves miners solving these cryptographic puzzles to create new blocks. Once a block is successfully mined, it is added to the blockchain and must be verified by the majority of nodes within the network. This verification is supported by consensus protocols like Proof of Work, which help validate legitimate transactions and identify any malicious activity within the chain.
Problem Definition and Advantages of Blockchain
Traditional transaction systems face several challenges, including the limitations of cash, which is typically used for low-value, local transactions. These systems often involve third-party verification, leading to transaction delays and added complexity, and the necessity of third parties introduces additional layers of trust and cost. Blockchain technology addresses these issues through its distributed ledger architecture, which is shared across all nodes and updated in real-time without central control, thus enhancing cost efficiency by eliminating the need for third-party verification and enhancing security as transactions are cryptographically secured and difficult to tamper with. The benefits of blockchain are substantial, offering significant time savings as transactions can be processed more quickly without a central authority, cost reductions by eliminating intermediaries, and enhanced security, making the system highly resistant to tampering and cyber threats.
Methodology
Blockchain Setup
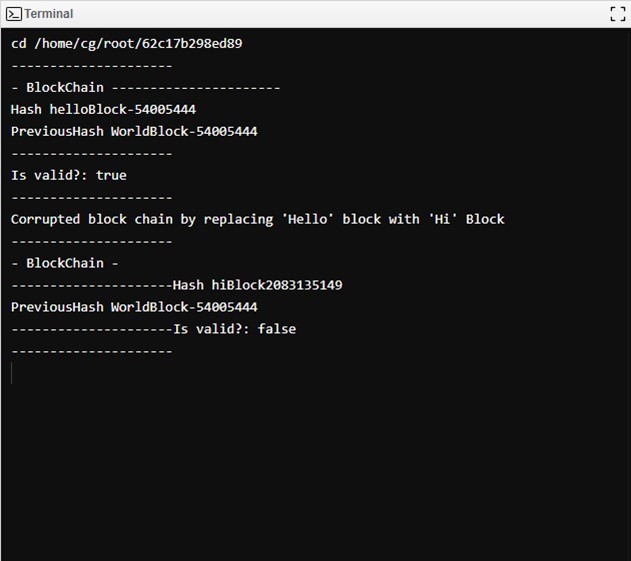
The experiment conducted aimed to demonstrate the immutability and integrity verification features of a blockchain implementation.A simple blockchain was initialized, consisting of blocks that include data, a unique hash (that represents the digital fingerprint of each block), and the hash of the previous block (linking it to the chain).
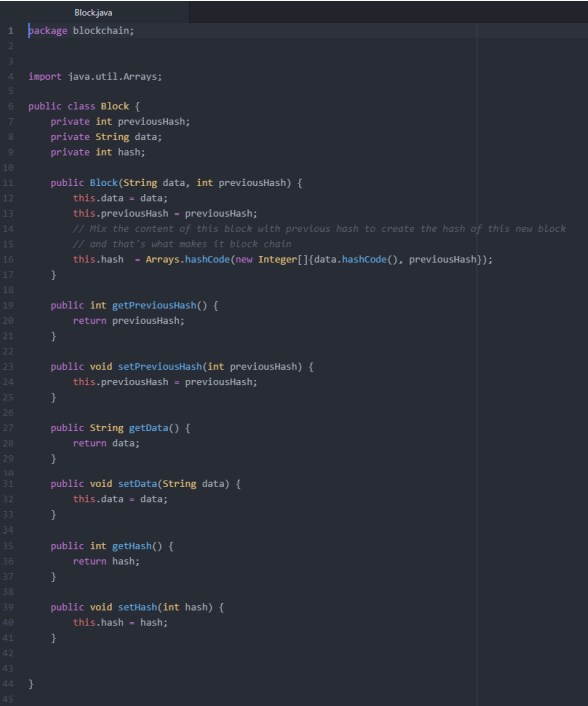
Validation Process
To maintain the integrity of the blockchain and ensure its trustworthiness, we implemented a sophisticated validation function. This function was designed to perform a thorough examination of the blockchain by verifying that each block's previous hash matches the hash of the immediately preceding block. This step is crucial as it ensures the continuity and unbroken chain of the blockchain, confirming that each block is correctly linked to its predecessor. The validation mechanism thus acts as a guardian of the blockchain's integrity, ensuring that all transactions recorded in the ledger are both accurate and unaltered from their original form.
Corruption Simulation
To test the resilience of our blockchain against potential security threats, we conducted a deliberate corruption simulation. In this phase, we altered the data within a specific block, changing its contents from "Hello" to "Hi" without updating the corresponding hash values and the links that connect the blocks. This type of simulation is critical for assessing the blockchain's vulnerability to unauthorized changes and ensuring that our system can detect and respond to tampering attempts.
Following the deliberate corruption of the blockchain, we reactivated the validation function to reassess the integrity of the chain. This revalidation process is crucial for detecting any discrepancies introduced during the corruption simulation. The function's ability to identify and flag the altered block as invalid underscores the robustness of the blockchain's security measures, demonstrating its capacity to detect unauthorized alterations and affirming the system's reliability and the effectiveness of its safeguard mechanisms. Through this comprehensive testing and validation framework, we emphasize the reliability of blockchain technology as a secure digital ledger system.
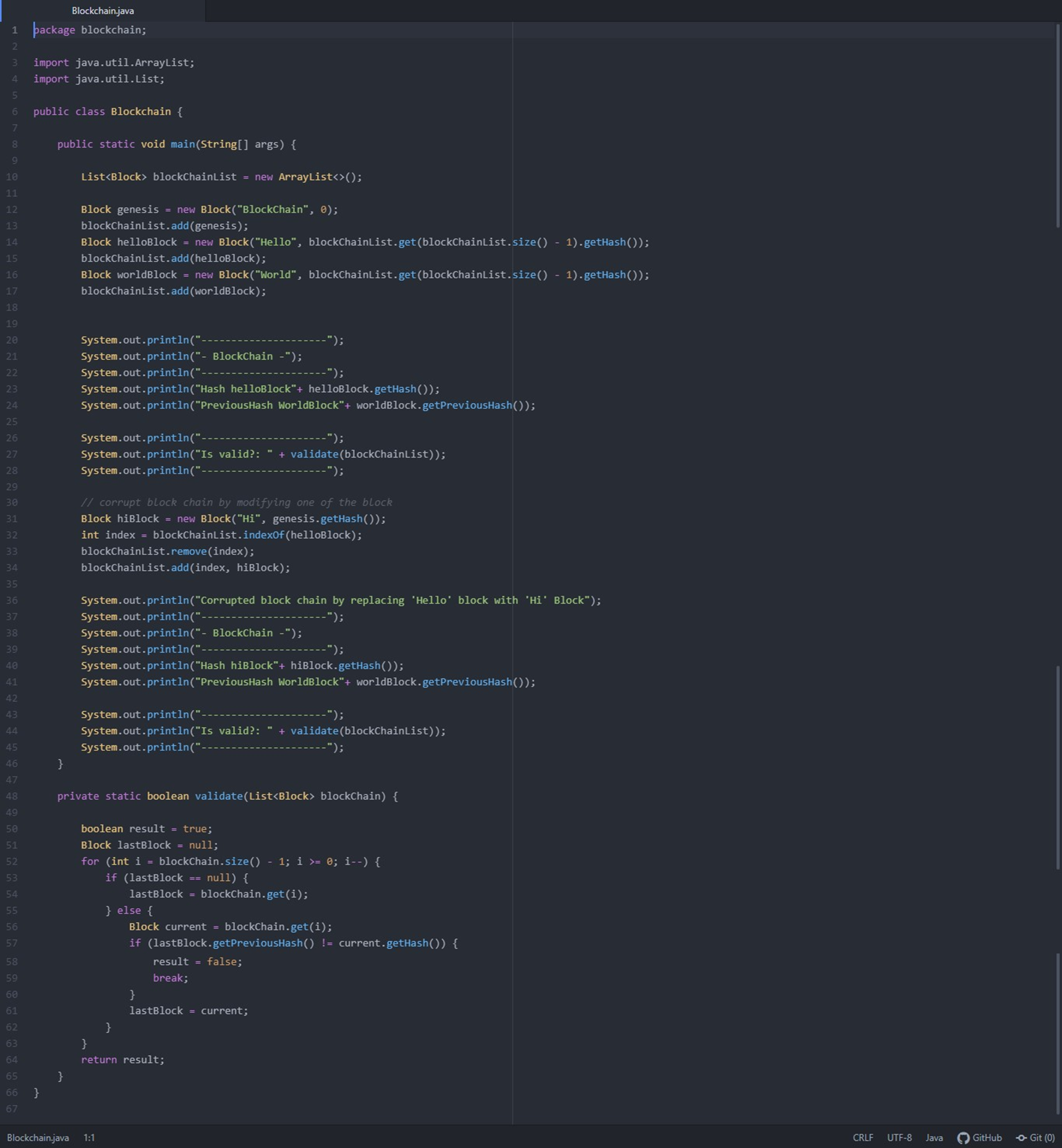
Results and Conclusion
Initially, the blockchain validated as true, indicating that the integrity was intact and all blocks were correctly linked. However, after the data modification, a revalidation process revealed a failure, denoted by a validation status of false. This indicated that the alteration was successfully detected due to a hash mismatch, showcasing the blockchain's sensitivity to unauthorized changes.It demonstrates that blockchain is an effective technology for scenarios where security and accuracy are paramount, capable of detecting tampering effortlessly. This makes it suitable for applications requiring uncompromised data security, such as in financial sectors, contract management, and other legal documentation processes.